Generates data erasure reports for audit trails with the option to customize & save reports in formats like PDF, CSV, & XML.
LA eCycle
Data Destruction Services
Don’t leave your sensitive data to chance. Whether it’s a single hard drive or an entire rack of servers, we offer physical data destruction you can trust. On-site or at our facility — your data is destroyed in minutes, with full certification.
Whether you drop it off or need on-site service, we’ll destroy your data while you watch.
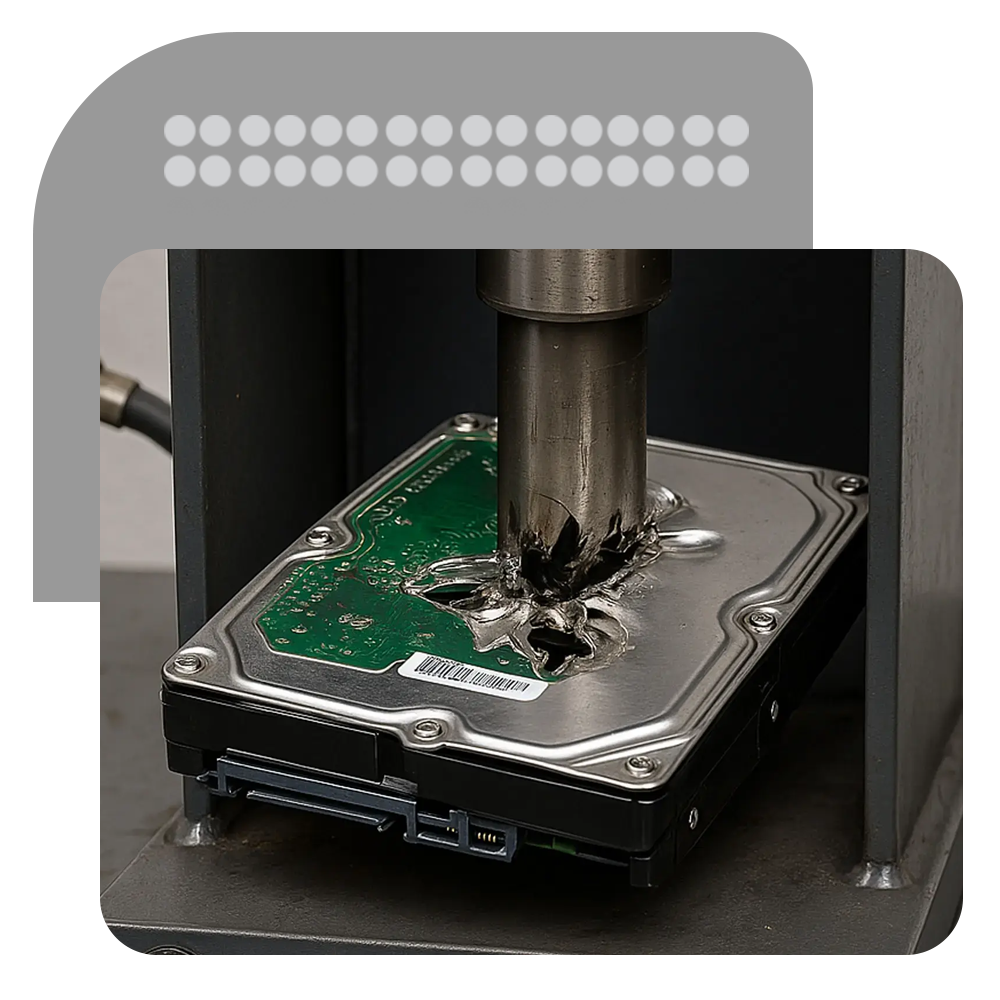





On-Site Data Destruction Services

Full Visibility
Watch your hard drives and devices being destroyed in real-time for complete peace of mind.
Regulatory Compliance
Stay aligned with data disposal regulations enforced by the FTC and other industry-specific standards.
Total Control
Nothing leaves your premises without being fully shredded — ensuring your sensitive data is completely unrecoverable.
Convenience & Security
Eliminate the risk of transporting data-rich hardware to another location. We bring the solution to your doorstep.
Device Tracking & Documentation
What We Destroy
Secure destruction for a wide range of electronics and digital media
- Computer (Mac & PC)
- Chromebook
- Server
- Hard Drive & SSD
- NVme & M.2
- SAN, NAS, DAS
- Smartphone & Tablet
Whether you’re a home user, small business, or enterprise-level organization, LA eCycle ensures your IT assets are completely destroyed and never return to the data stream.

Certificate of Destruction
A formal record of your secure disposal.
After each data destruction service, LA eCycle issues a Certificate of Destruction that details:
- The date and time of service
- The type and quantity of devices destroyed
- Serial numbers and other identifying info
- The destruction method used
This certificate is essential for demonstrating compliance with data protection laws and internal policies — and should be saved for your records in case future verification is needed.
Responsible Electronics Recycling
Recycling with LA eCycle is safe, sustainable, and free.
Proper e-waste recycling helps:

Preserve Natural Resources by reducing the need to mine new materials

Protect the Environment by keeping toxic substances like lead and mercury out of landfills

Recover Valuable Materials such as metals and plastics for reuse

Promote Sustainability by lowering energy use and carbon emissions

Certified Data Erasure You Can Trust

Secure Erasure
LA eCycle securely erases sensitive data beyond the scope of recovery from SSD, HDD, PC, Mac (with M1, M2, M3, T1 & T2 chips), Chromebook & Server.
Global Standard
Supports Global Wiping Standards LA eCycle follows up to 24 International erasure methods & standards, including NIST 800-88 Clear, NIST Purge, DoD 3 & 7 Passes, etc.
24 Global Standard
- NIST 800-88 Clear
- NIST 800-88 Purge
- US - DoD 5220.22-M (3 passes)
- US - DoD 5220.22-M (ECE) (7 passes)
- US - DoD 5200.28-STD (7 passes)
- Russian - GOST R 50739-95 (2 passes)
- B. Schneier's Algorithm (7 passes)
- German Standard VSITR (7 passes)
- Peter Gutmann (35 passes)
- Peter Gutmann (35 Passes)
- US Army AR 380-19 (3 passes)
- NATO Standard (7 passes)
- US Air Force AFSSI 5020 (3 passes)
- Pfitzner Algorithm (33 passes)
- Canadian CSEC ITSG-06 (1-3 Passes)
- NSA 130-1 (3 passes)
- British HMG IS5 (3 passes)
- Zeroes
- Pseudo-Random
- Pseudo-Random & Zeroes (2 passes)
- British - HMG IS5 (Baseline Standard)
- NAVSO P-5239-26 (3 passes)
- NCSC-TG-025 (3 passes)
- BitRaser Secure & SSD Erasure
- +5 Customized Algorithms
How it works?
Secure On-Site Data Destruction Process
Designed to meet strict compliance needs, including HIPAA, MPAA, FACTA, GLBA, and more.
1. Pre-Service Planning (Optional)
Inventory list is reviewed or created before arrival.
Client provides requirements based on industry standards.
2. Onsite Arrival
Our team arrives at your location with necessary equipment.
3. Authorized Personnel Verification
Only designated staff are permitted to release or sign off on assets.
4. Chain of Custody Initiated
Each item is logged and tracked through the entire destruction process.
5. Secure Handling & Containment
Devices are placed in locked, tamper-proof containers until destruction (if required).
6. Serial Number Recording
We document all serial numbers for traceability and client reporting.
7. Data Sanitization (If Requested)
Devices may be wiped using NIST 800-88 or DoD 5220.22-M standards prior to physical destruction.
8. Physical Onsite Destruction
Devices are shredded or crushed beyond recovery using industrial equipment.
9. Video or Photo Documentation (Optional)
Proof of destruction can be captured and shared upon request.
10. Client Witnessing (Optional)
Clients may oversee or record the destruction process onsite.
11. Certificate of Destruction Issued
Includes serial numbers, date, time, and method of destruction.
12. Responsible Recycling
All destroyed materials are sorted and processed at certified e-waste facilities.
FAQs
NSA-Compliant Data Destruction
At Los Angeles E-Waste, we offer NSA-compliant data destruction services that meet or exceed government standards. Our process involves physical destruction methods approved by the NSA/CSS Evaluated Products List (EPL)—including shredding, crushing, and degaussing—to guarantee data is unrecoverable, even by advanced forensic tools.
Whether you're a government agency, military contractor, or private company handling sensitive information, our NSA-level destruction solutions provide the highest level of security and peace of mind.
MPAA-Compliant Data Destruction
The Motion Picture Association of American (MPAA) enforces strict guidelines for content security, specially in media, post-production, and entertainment environments where protecting intellectual property is critical. These guidelines extend to the secure disposal of digital assets and storage devices to prevent leaks, piracy, or unauthorized distribution.
At LA eCycle we provide MPAA-compliant data destruction services designed for studios, production houses, media agencies, and content creators. We ensure all data—including unreleased films, scripts, media files, and project backups—is completely destroyed and irretrievable, following MPAA-recommended best practices such as physical destruction and certified data wiping.
Protect your creative assets and maintain industry trust with secure, standards-based data destruction.
NIST-Compliant Data Destruction
The National Institute of Standards and Technology (NIST) sets the benchmark for secure data disposal through its NIST Special Publication 800-88 Revision 1 guidelines. These standards outline the proper methods to sanitize data from electronic storage media to prevent unauthorized recovery and ensure regulatory compliance.
At LA eCycle, we follow NIST 800-88 compliant data destruction processes, including Clear, Purge, and Destroy methods based on the sensitivity of the data and the type of storage device. Our services cover hard drives, SSDs, servers, mobile devices, and more—ensuring data is permanently wiped or physically destroyed according to NIST recommendations.
Whether you're a business, healthcare provider, or government agency, our NIST-compliant services help you meet security, privacy, and audit requirements with confidence.
Data Destruction for Financial Institutions.
Financial institutions are legally obligated to protect sensitive customer data—even at the end of its lifecycle. Regulations such as the Gramm-Leach-Bliley Act (GLBA), Fair and Accurate Credit Transactions Act (FACTA), and FFIEC guidelines require that any data stored on hard drives, servers, or removable media be completely destroyed to prevent unauthorized access.
At Los Angeles E-Waste, we provide secure, compliant data destruction services tailored to banks, credit unions, lenders, and financial service providers. Our services meet or exceed industry standards, including NIST 800-88 and DoD data wipe methods, with options for on-site or off-site physical destruction, certified data wiping, and detailed audit reporting.
Whether you're decommissioning IT assets or clearing out outdated storage devices, we help ensure full compliance and protection of financial data—backed by Certificates of Destruction and chain-of-custody documentation.
What type of data destruction methods are outthere?
Shredding:
Physically grinds drives into fine particles, rendering recovery impossible.
Crushing:
Punctures and deforms internal platters with hydraulic force.
Degaussing:
Uses high-powered magnets to permanently erase all data from magnetic media.
Data Wiping Solution
Physical Destruction (Shredding)
Shredding (Physical Destruction)
Best for: Enterprises, Healthcare, Financial Institutions, Government Agency. We use industrial-grade shredders to grind hard drives and data storage devices into tiny, unrecognizable particles (typically <10mm). This is the most secure physical destruction method available.
Meets Standards:
- NIST 800-88 Purge
- DoD 5220.22-M
- NSA/CSS EPL Guidelines
Devices Supported:
HDDs, SSDs, backup tapes, flash drives, mobile devices, optical media
Post-Destruction Handling:
Shredded materials are recycled through R2-certified downstream partners.
Crushing (Hydraulic Punching)
Best for: On-Site Jobs, Remote Facilities, Mobile Data Destruction.
Our hydraulic crusher punctures and distorts the internal platters of hard drives and SSDs using over 12 tons of force. This renders the device unreadable and unusable.
Meets Standards:
- NIST 800-88 Clear
- DoD 5220.22-M (for platter destruction)
Devices Supported: - HDDs, SSDs, cell phones, tablets
- On-Site Option Available:
Watch destruction occur in real-time at your location.
Degaussing (Magnetic Erasure)
Best for: Sensitive Data on Magnetic Media
Degaussing uses a high-powered magnetic field to completely disrupt the magnetic domains on a drive, permanently erasing all data.
Meets Standards:
- NIST 800-88 Clear & Purge
- NSA/CSS EPL
- DoD 5220.22-M
Works on HDDs and magnetic tapes only — not effective on SSDs or flash memory.
Responsible Disposal:
Degaussed media is sent for physical recycling through certified partners.
Data Wiping (Software-Based Overwriting)
Best for: Asset Reuse, Lease Returns, Equipment Refurbishment.
We offer multi-pass data wiping using DoD and NIST-compliant software. This process overwrites all data multiple times to make recovery impossible — while preserving the hardware for reuse.
Supports Up to 24 International Standards:
- DoD 5220.22-M (3 & 7-pass)
- NIST 800-88 Clear & Purge
- British HMG IS5, German VSITR, Peter
- Gutmann (35-pass), and more Devices
Supported: HDDs, SSDs, PCs, Macs (including M1/M2/M3 chips), Chromebooks, servers.
📁 Deliverables: Detailed wiping reports with serial numbers Certificate of Data Erasure Optional audit logs (PDF, CSV, XML)

